Something about AppLocker

When configuring AppLocker there are several things to think about. AppLocker itself a tool from Microsoft integrated into Windows to allow Administrators and also Microsoft itself to block applications based on three different identifiers.
The Identifiers are:
- Path
- Hash
- Publisher
Microsoft does configure AppLocker with some Default rules if you wish to enable them.
The requirements to run AppLocker is at least Windows Pro edition.
Rules are enforced as a default, so if you apply rules then they are enforced, no rules mean nothing to enforce. So to first verify your rules please first set the AppLocker to Audit mode, this is done in the same place were you configure the rules itself.
Path
The Path rule checks for the path of an application, this can be easily circumvented if you can move or install an application outside of this specified path or filename.
Hash
A Hash rule is exactly meant to just verify the hash of an application to be blocked and nothing else, this is the most direct and specific rule options. But you need to be aware that this is somewhat work intensive because you need to keep the hashes up to date if they ever change.
Publisher
The Publisher rule is the most powerful in my opinion.
You can filter for a specific publisher based on the vendors Code Signing certificate for an application. But you can also make use of wildcards, so you can allow or deny specific application vendors, products, executables and down to the version or ranges of versions.
The AppLocker „Control Panel“
AppLocker policies are configured in three locations but basically these are just two locations.
- Domain Group Policy Management
- Local Group Policy
- Local Security Policies
The Local Group Policy and Security Policy do sync each other though. These Screenshots show you a brief overview of the options in the panel
Hidden Options
A hidden option which is hidden for a reason is the DLL Rule Collections.
This will degrade your systems performance and will audit every DLL to be loaded for an AppLocker Allow/Deny rule.
AppLocker Processing Rules
- A deny rule always overwrites an allow rule
- If a rule exists even if it is an allow rule is a implicit deny for everything else
- If a Exe Rule exists than all packaged Apps are blocked also until you allow the packaged app or allow every packaged app
AppLocker Event Log
You can find the Event Log for AppLocker in the Event Viewer at: Applications and Services - Microsoft - Windows AppLocker
And then you have a Log per Category in AppLocker
Use Case Examples
Blocking a specific group to execute an application
So you want to block a specific group to execute an application than you create a deny rule for the application targeted to the group, this is one of the easier things to do in AppLocker.
Allowing a specific group to execute an application
For example you want to deny users to execute well known browsers because you have a managed browser for your environment. Then you need to think out of the box because you can‘t just Deny the application and than allow it to a group, because a deny wins over an allow.
So how you do it ?
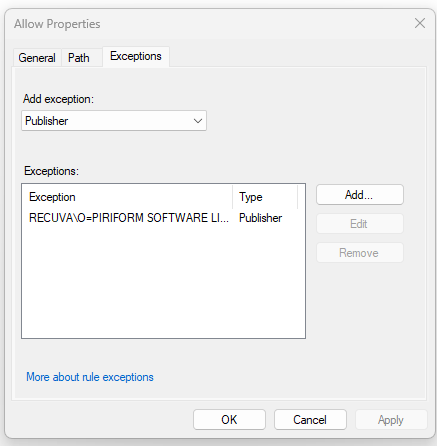
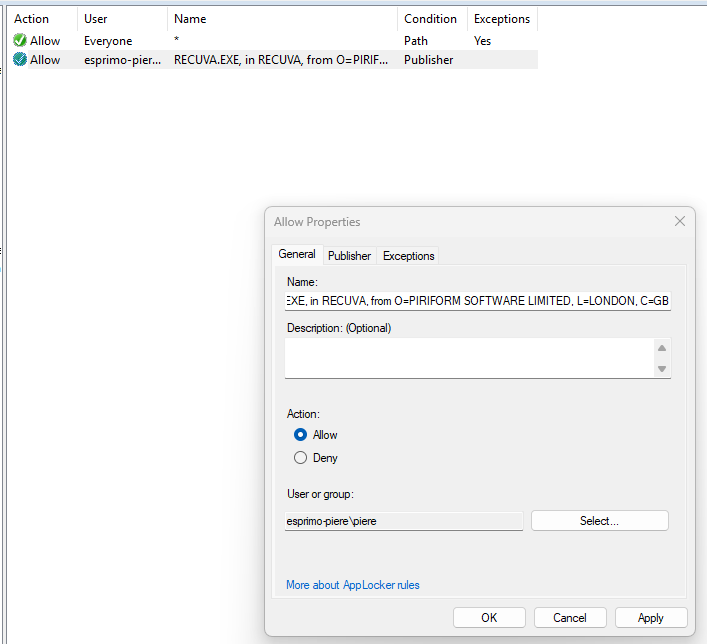
- You create a rule for Everyone to Allow Anything, this is done with a Path rule and the Path to be the wildcard symbol „*“.
- You then go into the Rule and under Exceptions place every Application you want to block, this works because you make an exception to an allow which then is implicitly denied.
- Now you create a Allow rule for the exact applications you just made an exception for in the Allow Everyone Anything rule and assign it to the group you wish to attach it to



Blocking vulnerable Applications
Here we make use of the Publisher rule, you can basically set the rule to allow anything of this Publisher and Application but deny access to applications with a version number below a specific point, combined with hash rules you have a pretty powerful Method of blocking vulnerable applications for your users.



